Please go to our Blogger site at blog.backspace.academy This site will no longer be updated.
Access an AWS S3 Bucket
Not only can we use our CognitoID temporary credentials do access CongitoSync, we can use it access many other AWS resources.
First we need to modify our apps IAM role to allow access to S3. It is extremely important when doing this to ensure that the user only has access to a folder with their CognitoID. Otherwise someone can maliciously dump a few terabytes into your S3 bucket or even worse start deleting objects.
Go into the AWS IAM Console.
Click on roles and select the IAM role you created.
Click on Manage Policy
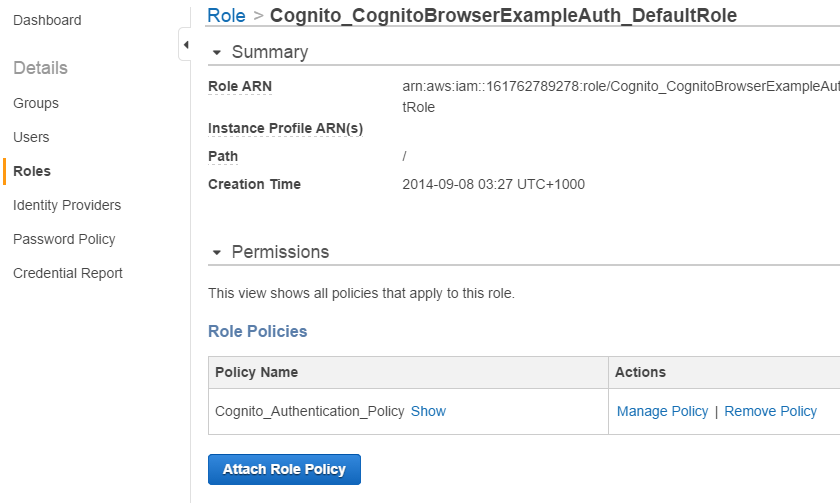
Now change the policy to allow access to a folder in the user's CognitoID. It is very important to ensure that the "Version": "2012-10-17" statement is included otherwise the policy variables will not be recognised. Then click on Apply Policy.
To demonstrate we are going to call createS3 to create a folder in the user's name and add an object to it. Open app.js in your editor and add a call to the createS3 in the callback of addRecord().
Next you need to go into the AWS S3 Console and create a bucket.
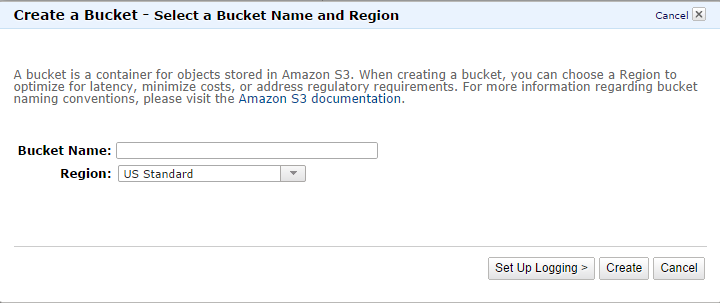
Now lets add a folder to the bucket in the name of the user's CognitoID. Then we will add a text file to it with the contents "Hello". You need to change the bucket name to the name of your bucket.
Now you can build and run your app. You should be able to login to Facebook and access S3.
Its all up to you now to identify how you are going to use this power! Maybe some big data crunching with Elastic Map Reduce, backup to Glacier or some heavy scientific processing with EC2.
Enjoy!